基于本地大模型的答题解决方案
2025年12月13日小于 1 分钟
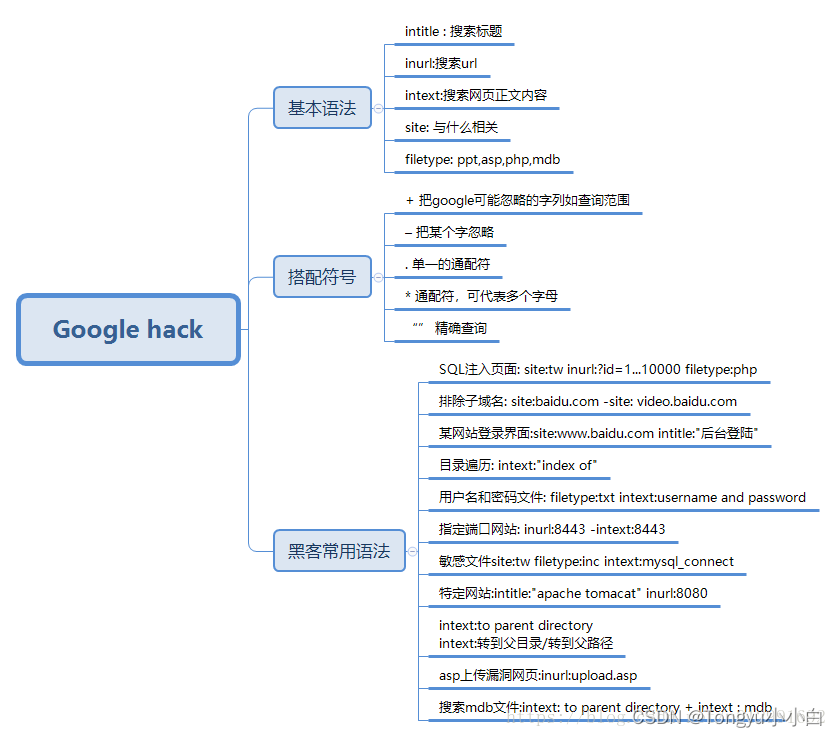
用于查找含有该值的所有url网址网页。 例:inurl:mail(可找一些免费邮箱)
找出和该网址类似的网站,比如想知道和amazon.com类似的大型网络书店有哪些时输入
amazon.com网址。例:related:amazon.com
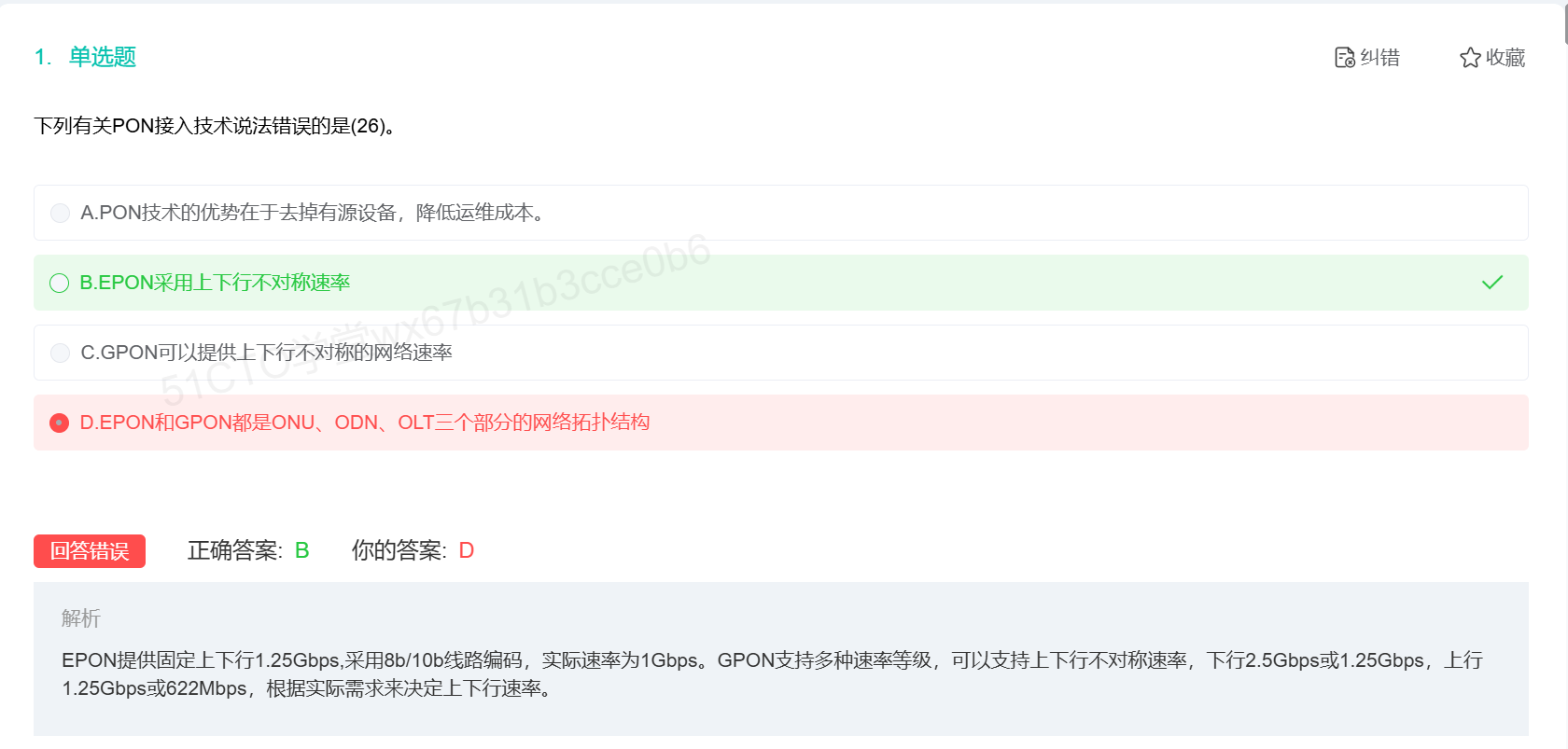
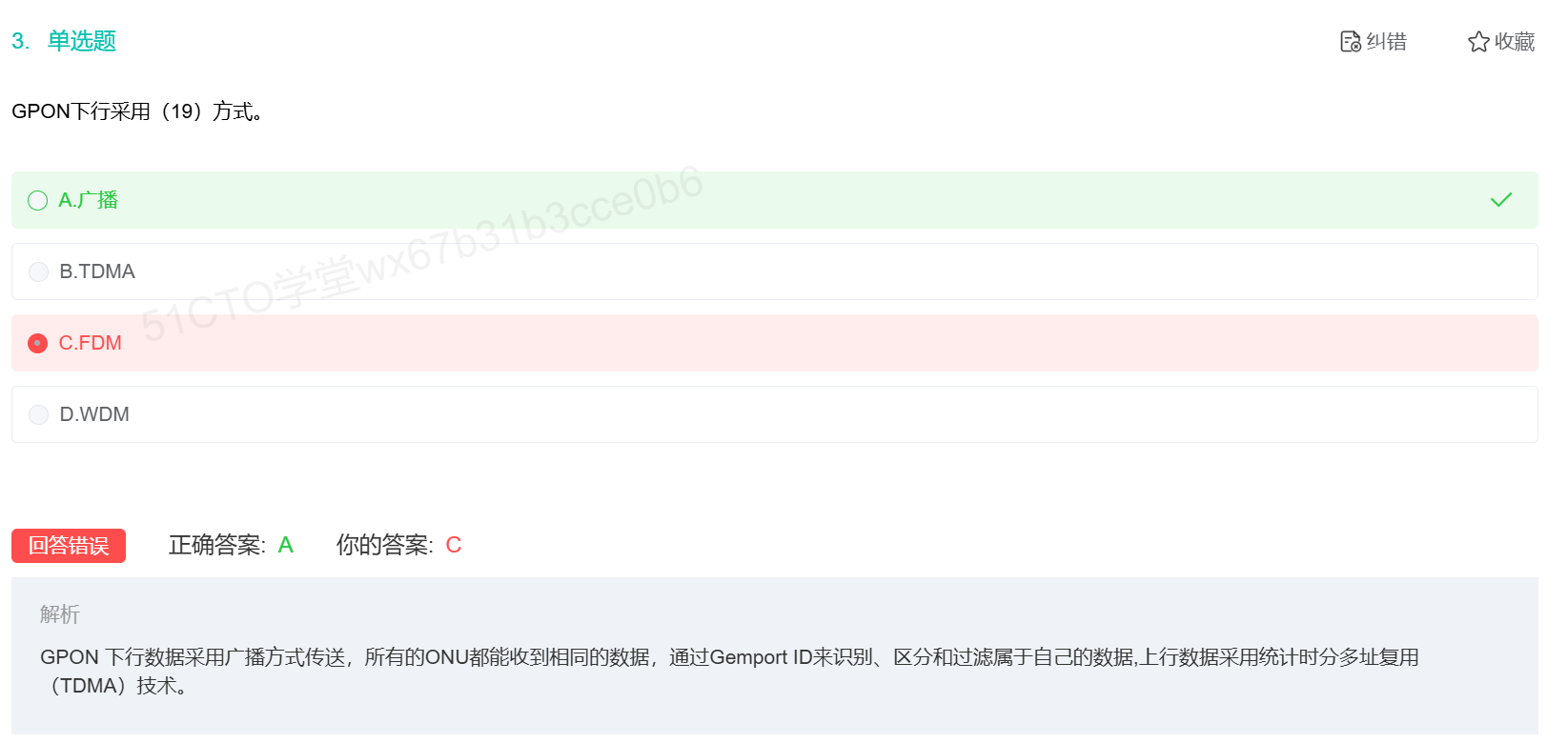
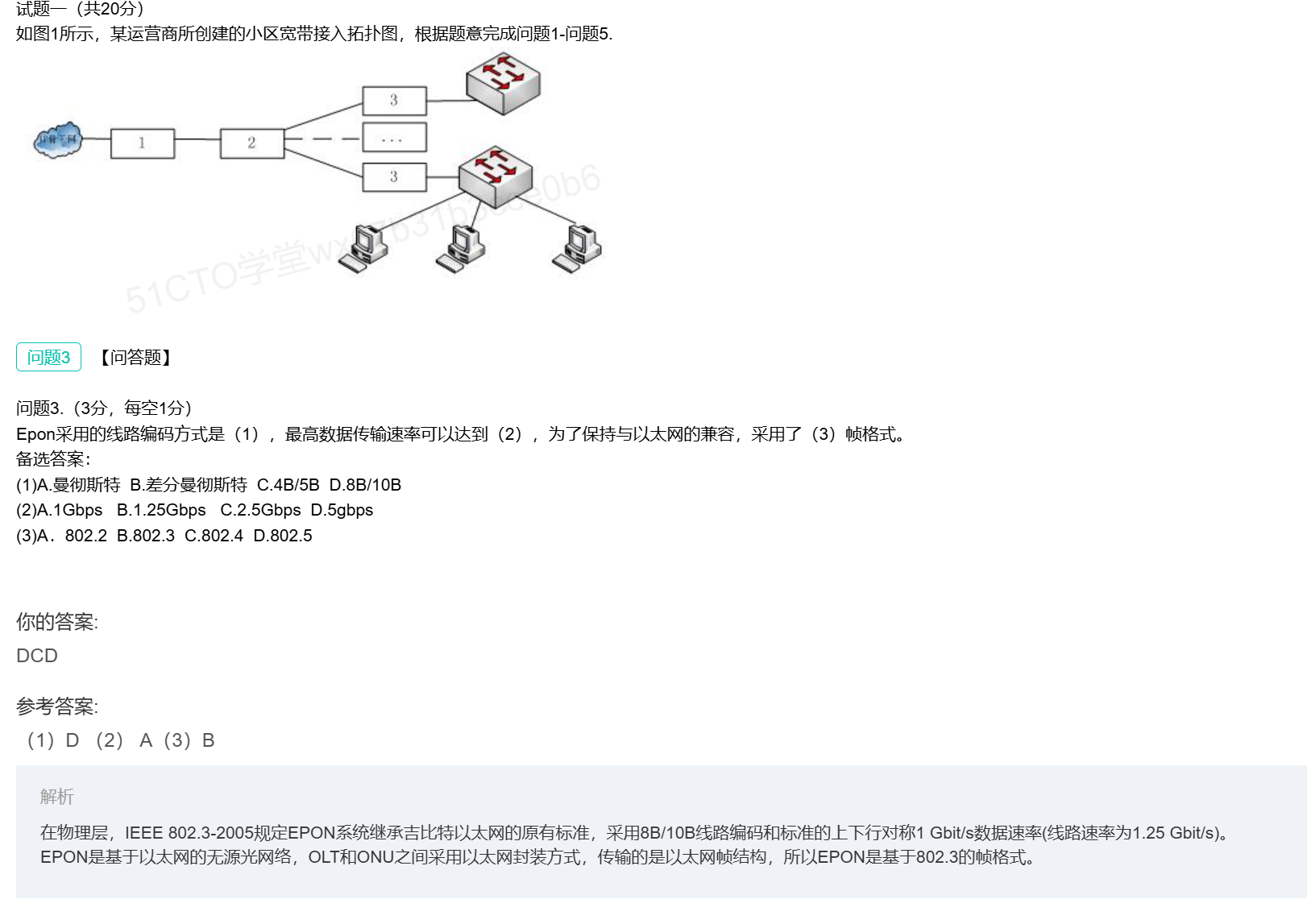
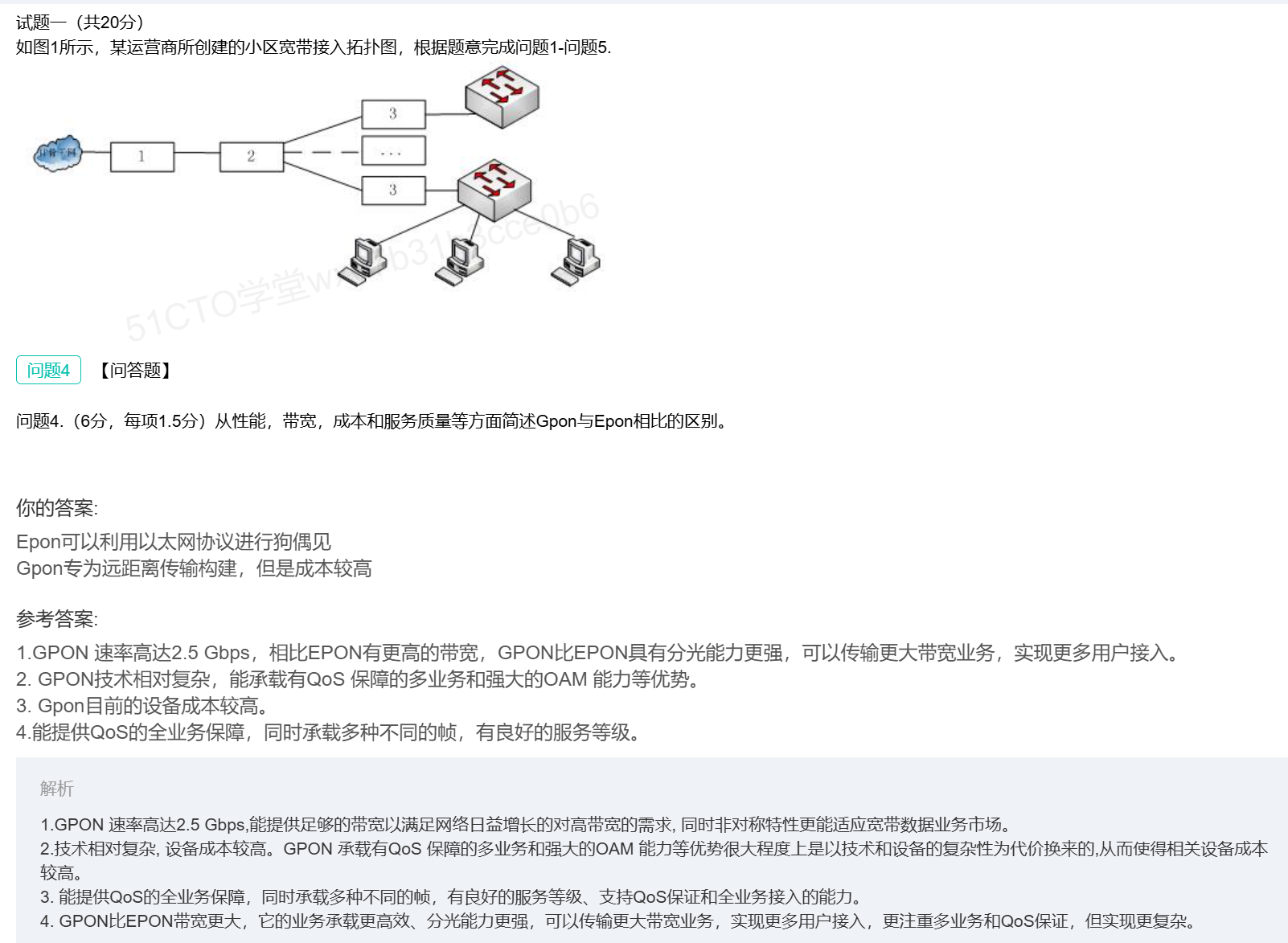
GPON竟然采用时分复用技术进行上传
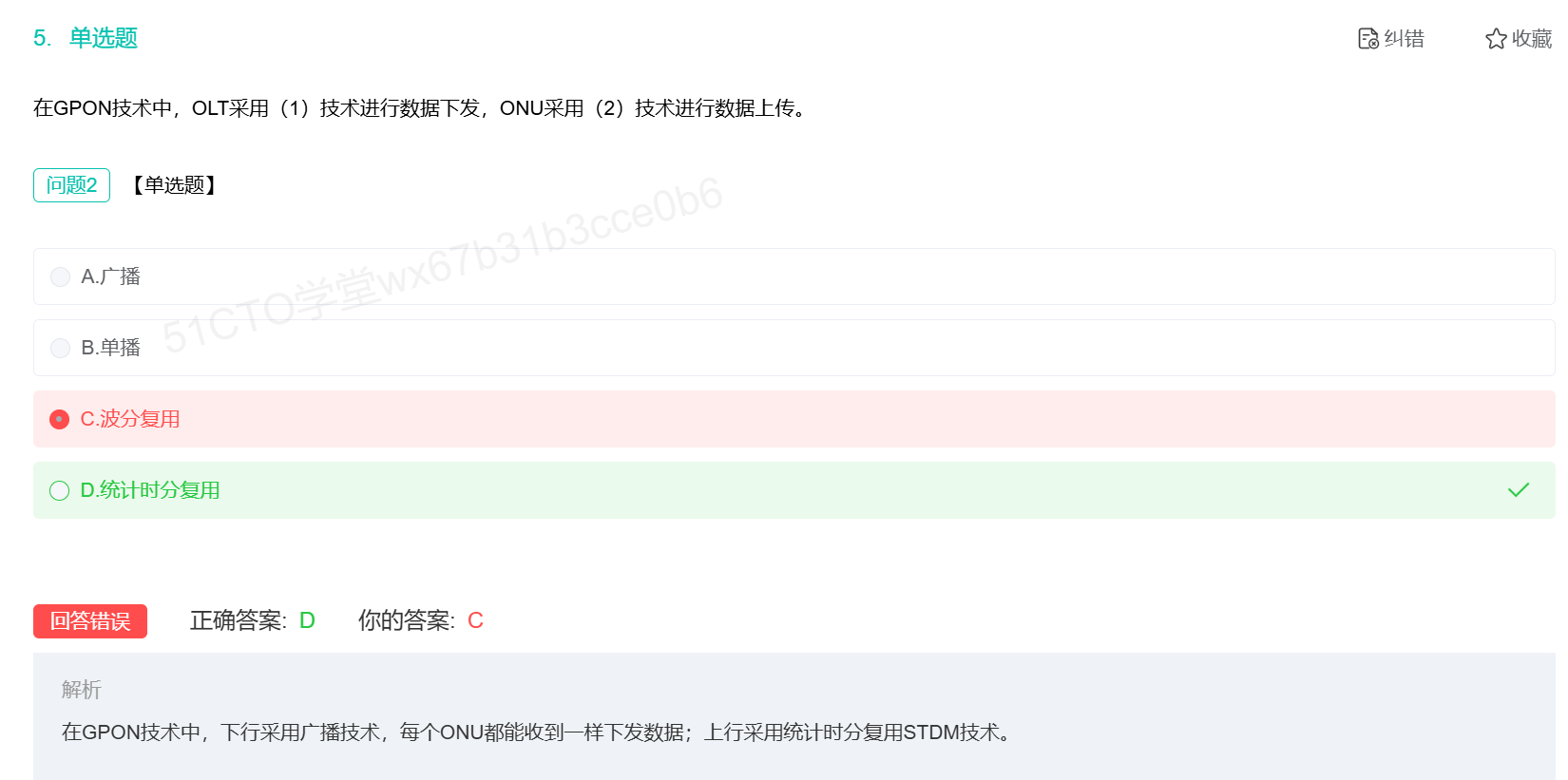
TDMA是什么?
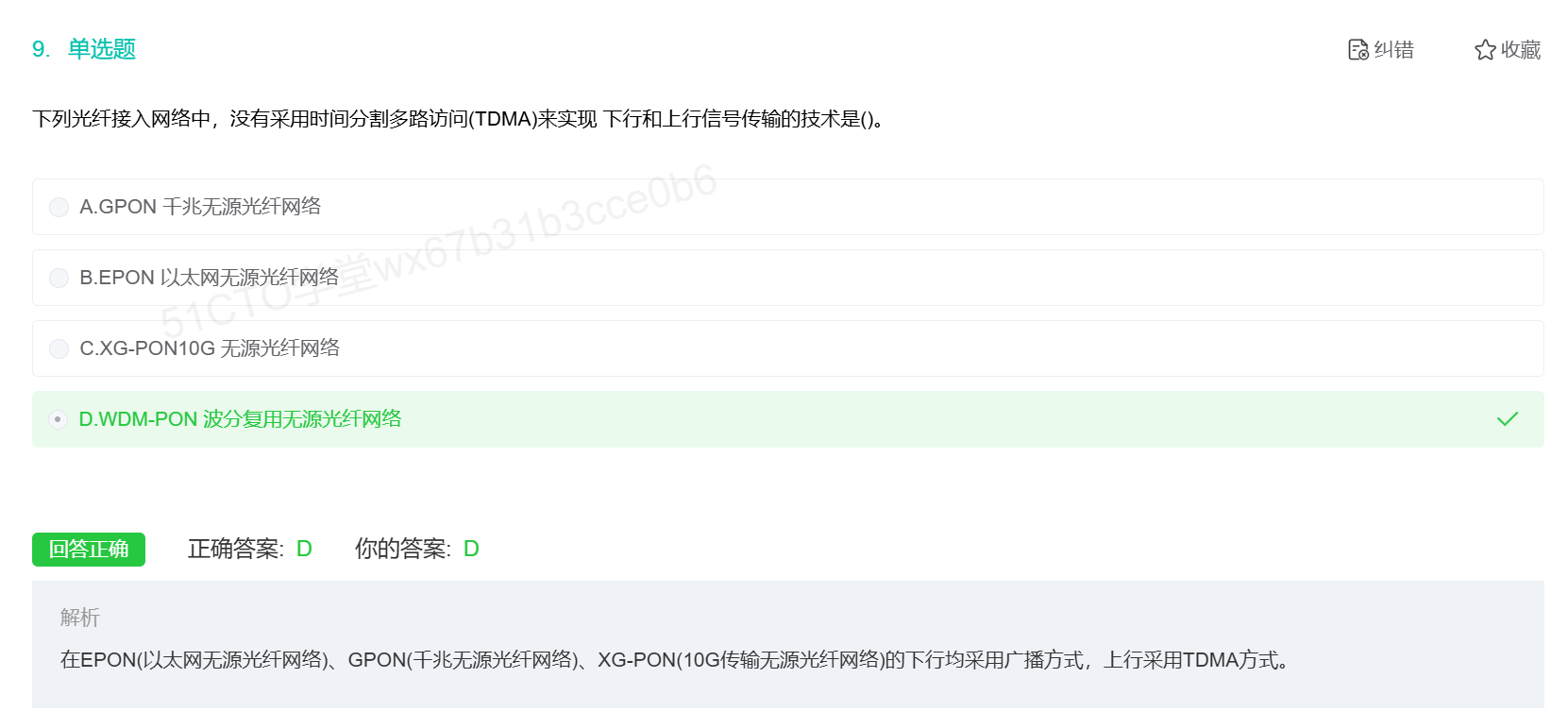
PON与交换机结合的有趣理论
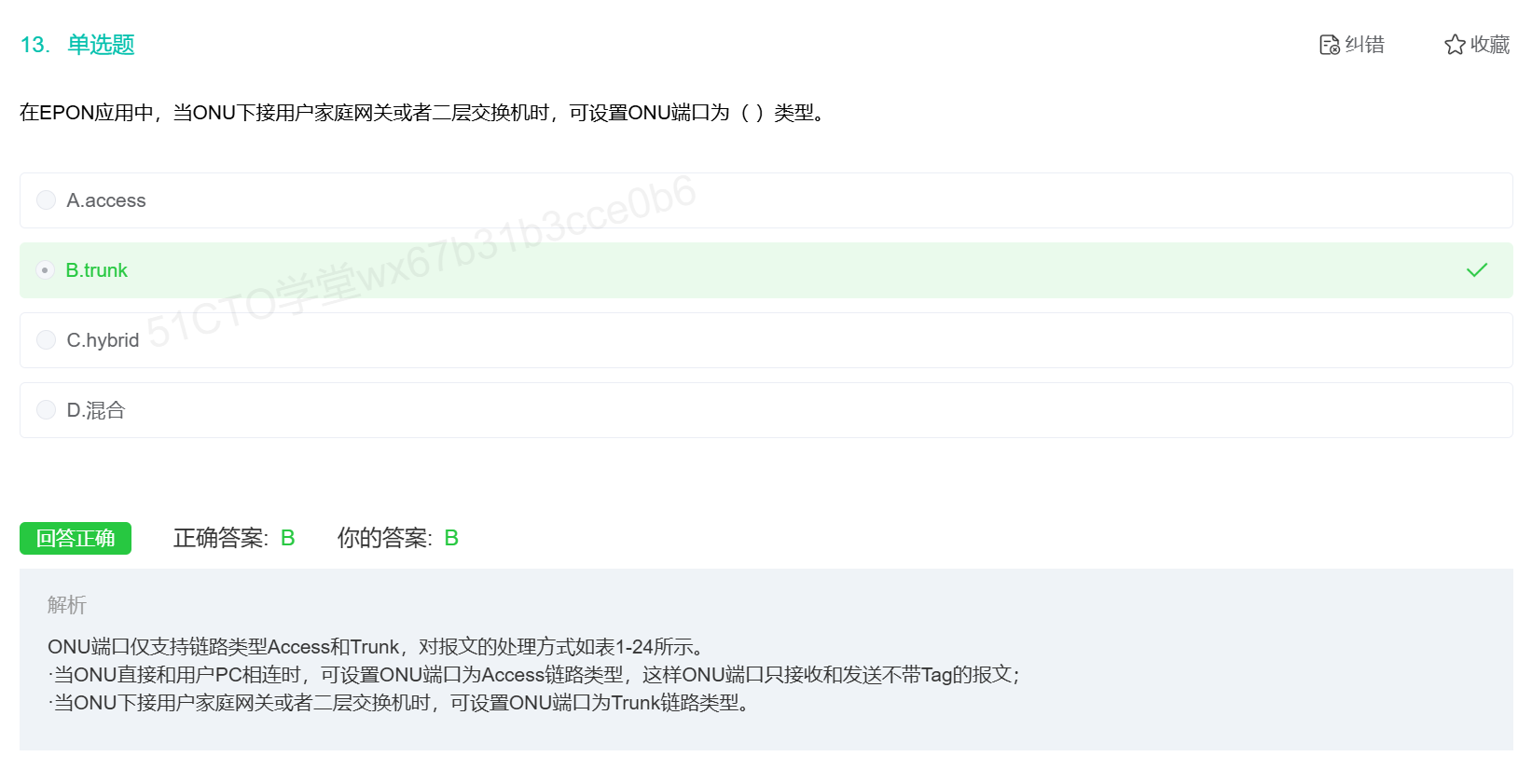
很不错的题,用于了解PON的基础概念
PON接入的三个组成部分
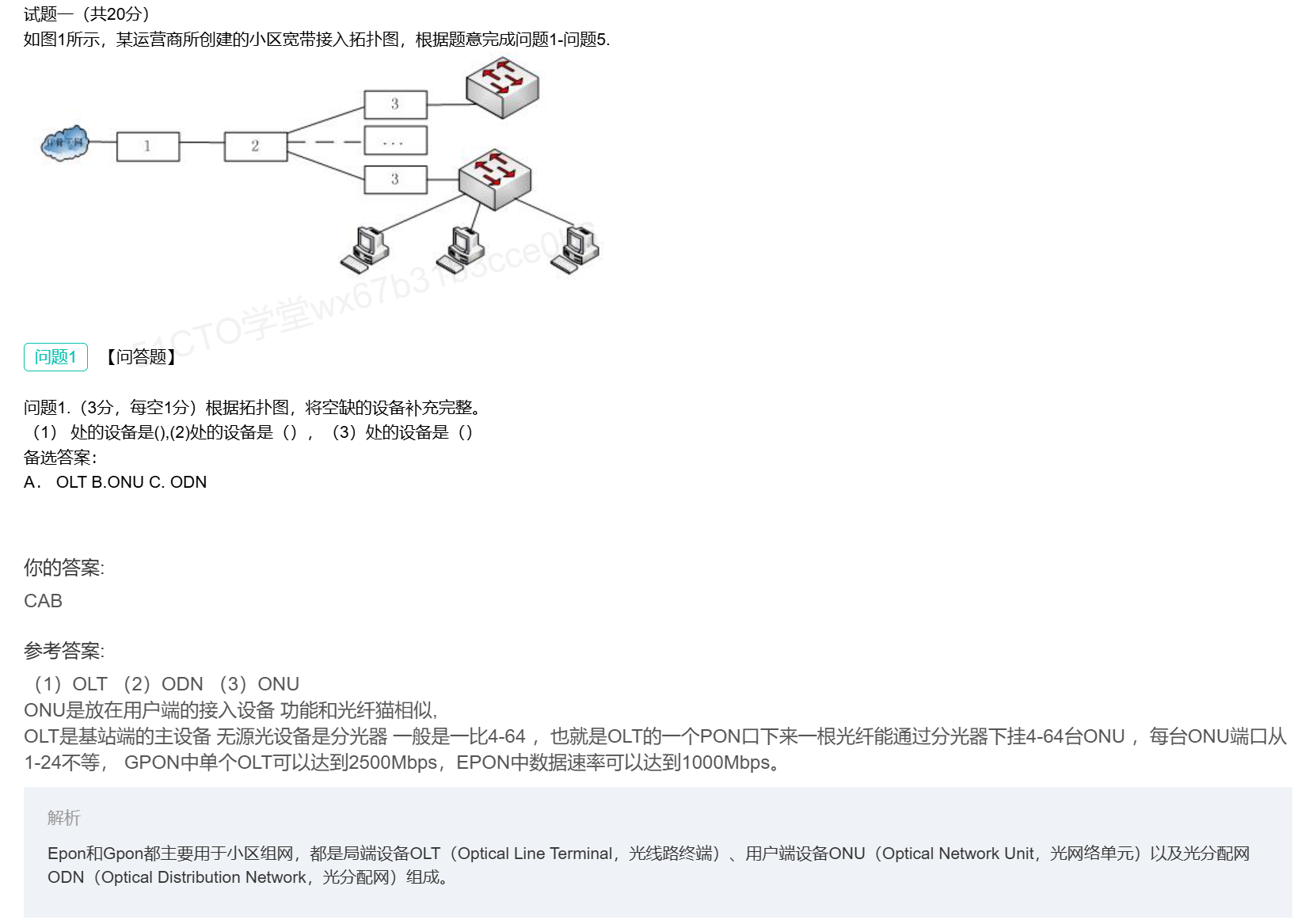
EPON特点
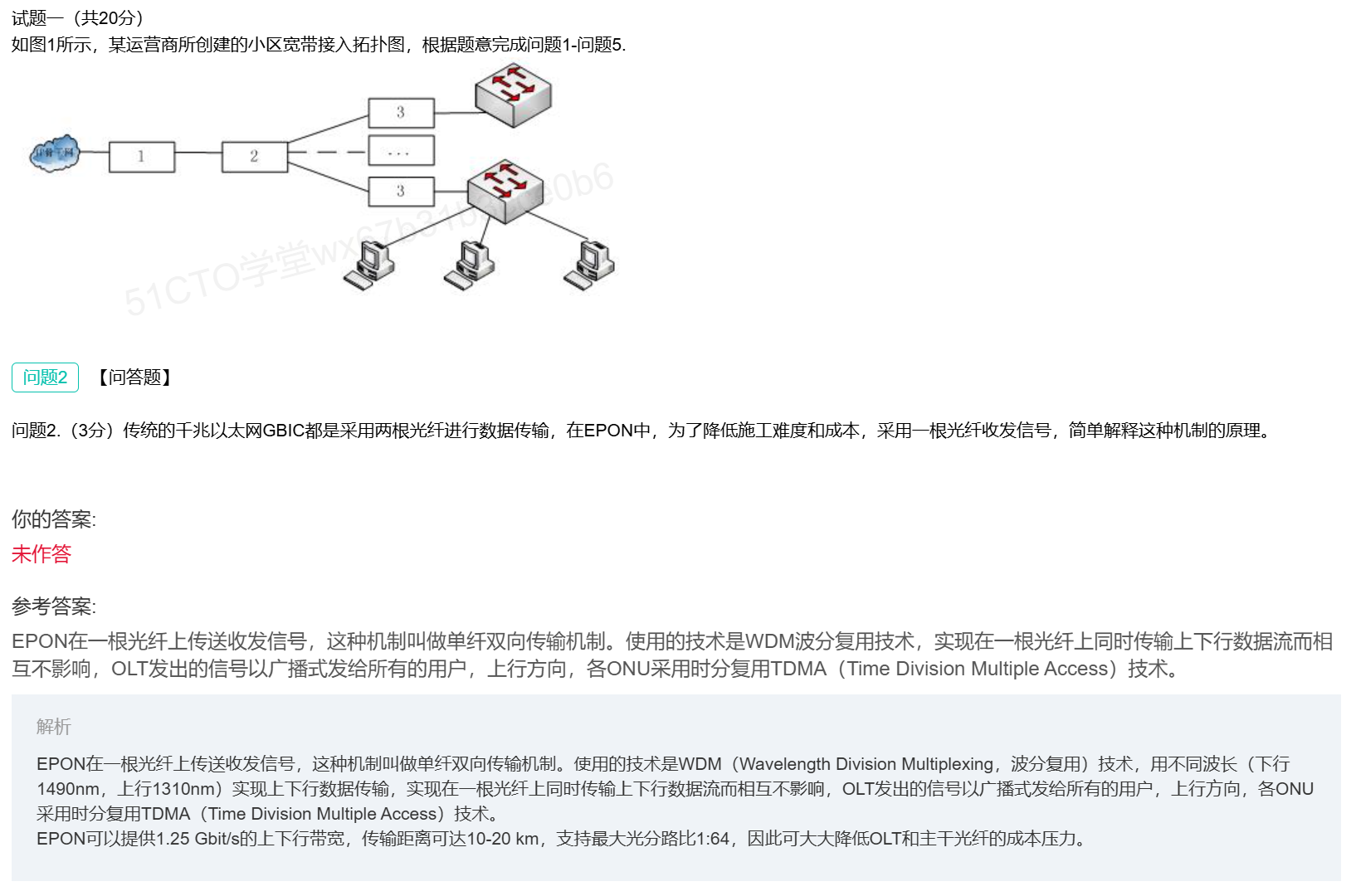
EPON原理
GPON特点
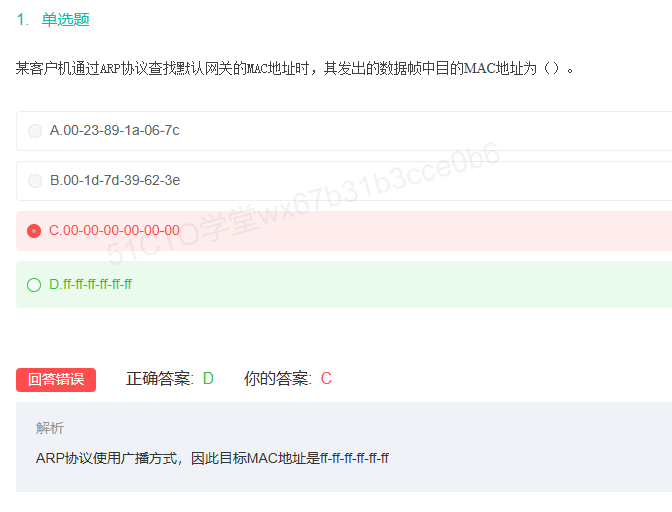
ff-ff-ff-ff-ff是mac广播地址
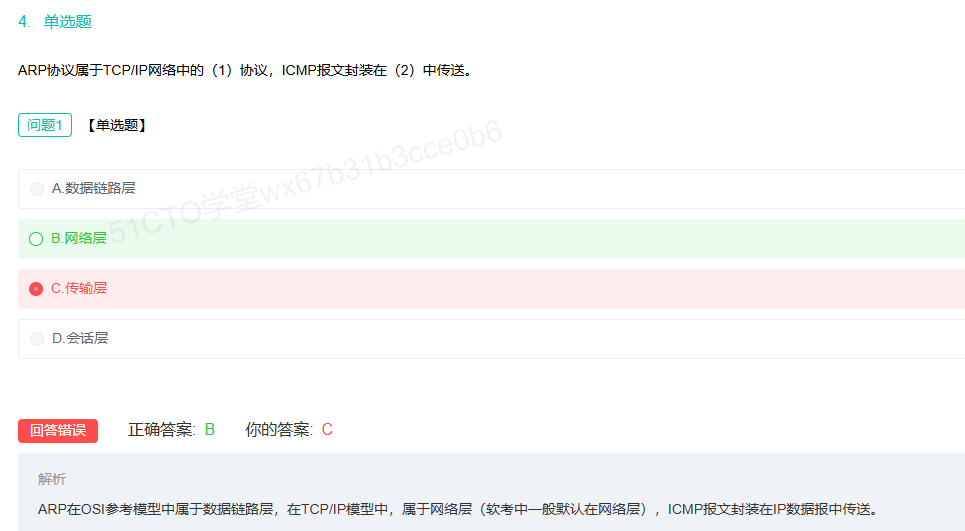
ARP属于网络层地址中
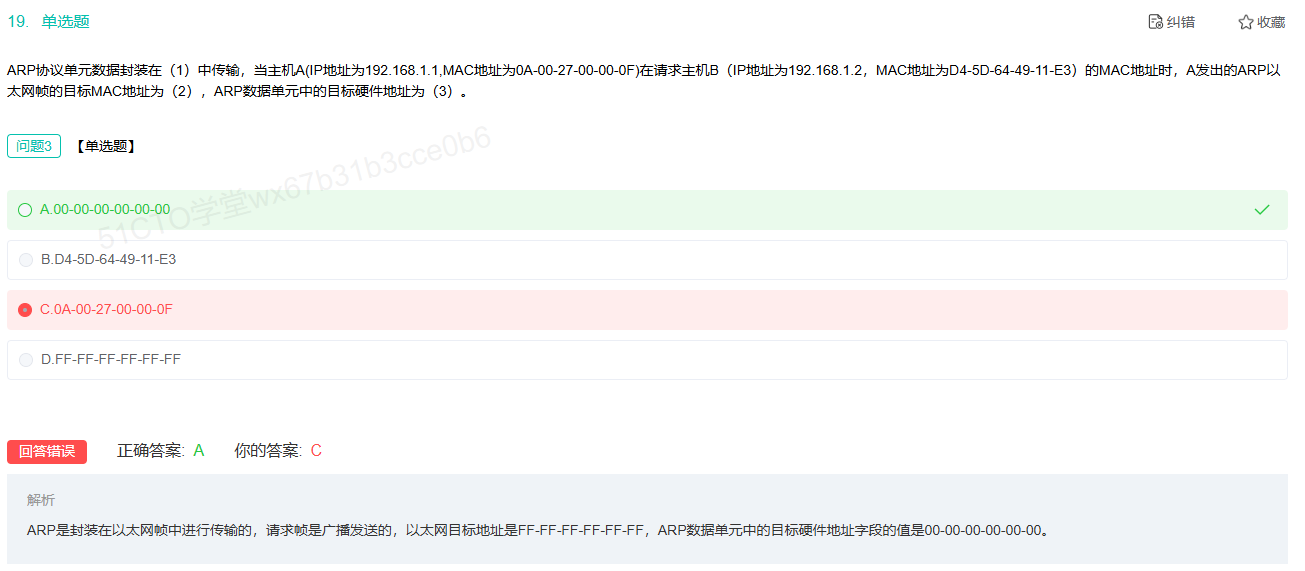
广播中的ARP协议以太网地址为FF-FF-FF-FF-FF-FF,目标硬件地址字段值为00-00-00-00-00-00
开启端口(端口配置)
undo shutdown
关闭端口(端口配置)
shutdown
主根设置
stp root primary
次根设置
stp root secondary
手动调整根端口选举(端口配置,自动规则:对端端口id小的成为根端口)
stp port priority 0设置优先级为0
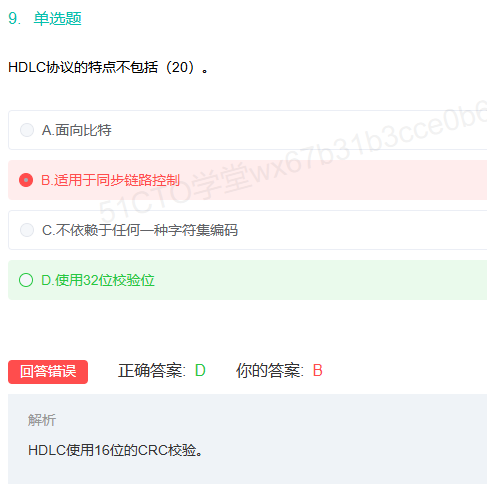
信息帧仅捎带差错控制,例如CRC校验
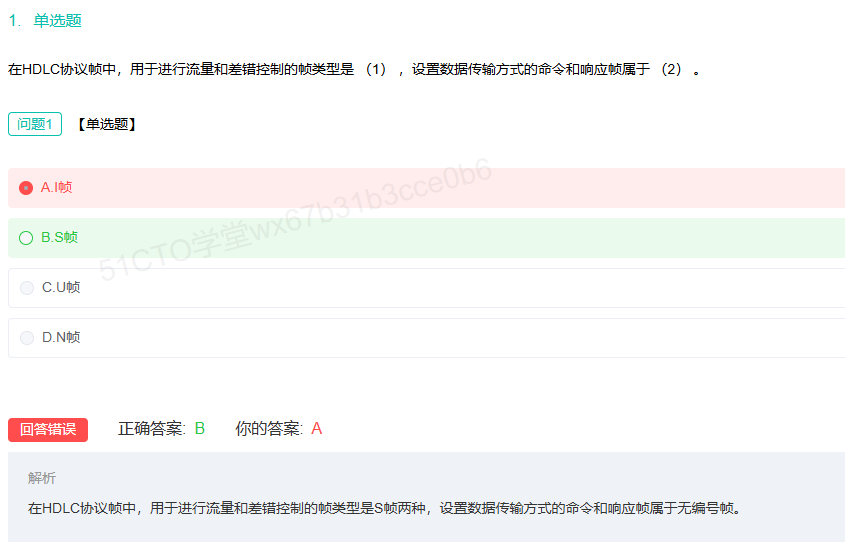
监控帧和无编号帧不要混淆
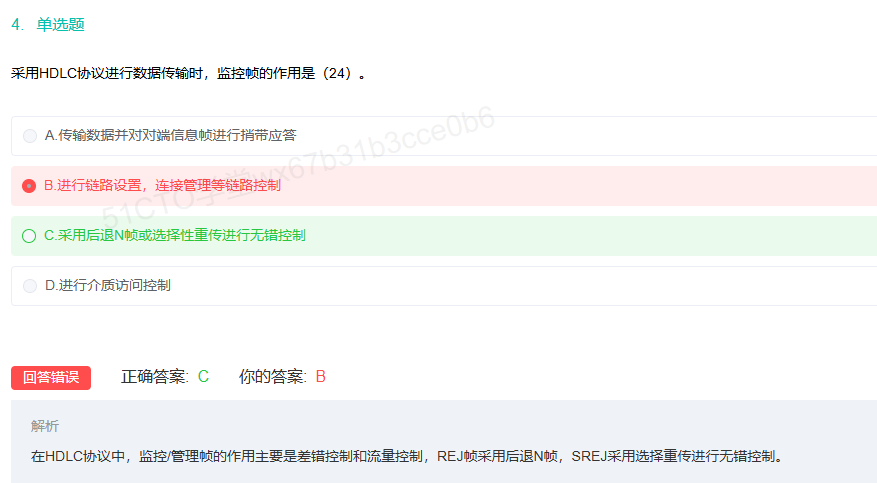
关于HDLC的ARQ机制的细节补充
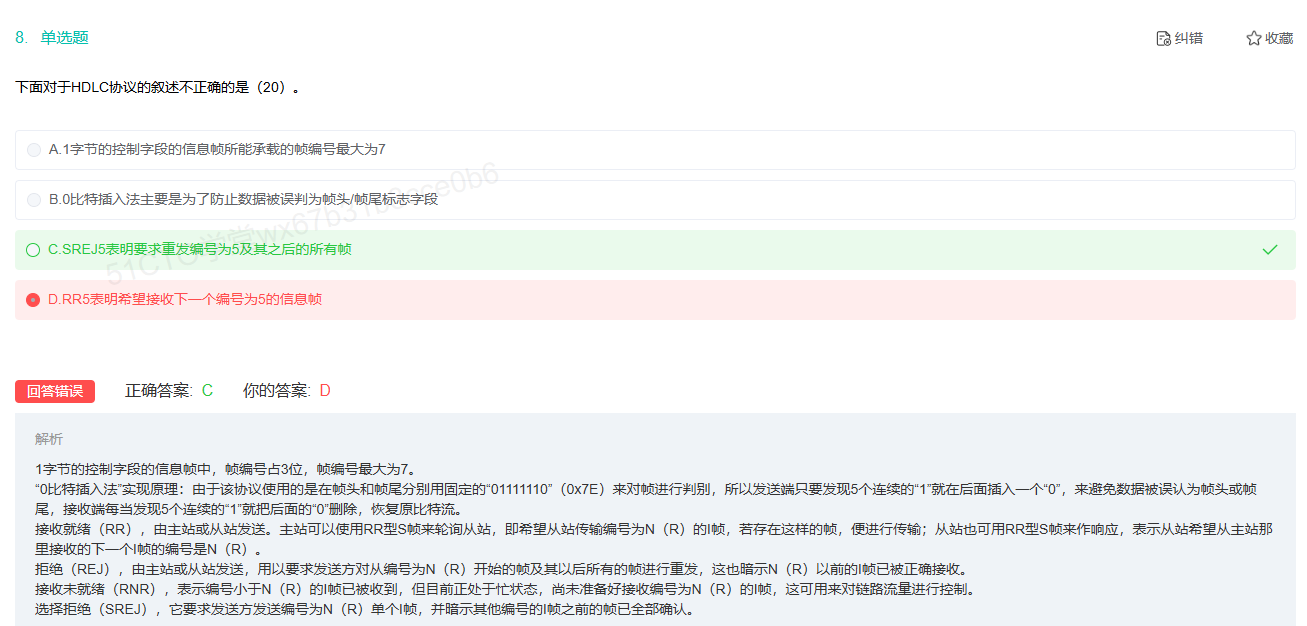
HDLC的校验方式为CRC16
关于0比特填充的更多信息

fscan扫描,爆出mssql弱密码san:1
使用sqsh连接mssql
sqsh -S 10.99.xx.xx -U sa -P 1